Aktuális kutatási területek
OT Cyber Range fejlesztése és az OT biztonság jelentősége
Az ipari rendszerek (Operational Technology – OT) digitális védelme egyre nagyobb jelentőséggel bír a kritikus infrastruktúrák fenntarthatósága és biztonsága szempontjából. Míg a klasszikus IT rendszerek biztonsága már jelentős figyelmet kap, az OT rendszerek – például ipari vezérlők, SCADA rendszerek, PLC-k – gyakran elavult, vagy nem megfelelően védett architektúrákra épülnek. A fenyegetettség mértékét növeli, hogy ezek a rendszerek egyre inkább kapcsolódnak IP alapú hálózatokhoz.
A témához kapcsolódó szakdolgozat / diplomamunka témák ITT...
Agentic AI alkalmazása a kiberbiztonságban / Agentic AI in Cybersecurity
Az Agentic AI rendszerek – vagyis autonóm, célorientált mesterséges intelligenciák – egyre fontosabb szerepet töltenek be a kiberbiztonság területén. Míg a klasszikus gépi tanulási rendszerek passzív mintázatokra épülnek, az agent-alapú rendszerek képesek adaptív döntéshozatalra, tanulásra és akár interaktív cselekvésre is komplex környezetekben. Kutatásunk ezen technológiák bevezetését célozza különféle kiberbiztonsági területeken, a gyakorlati alkalmazásokra koncentrálva. Jelenlegi fókuszterületeink:
A témához kapcsolódó szakdolgozat / diplomamunka témák ITT...
SOC — labor továbbfejlesztése
Az egyik fő kutatási irányunk az egyetemen, nyílt forráskódú eszközökkel felépített, jelenleg is működő Biztonsági Műveleti Központ (SOC) bővítése, folyamatos fejlesztése. Ez elsősorban a SOC-ba kötött eszközökből érkező napló és monitorozási adatok alapján történő optimalizálást jelenti, de ugyanakkor a támadás detektálás szélesebb körű megoldásaival is foglalkozunk. Egy általános hálózatban védelmi oldalon használt eszközök, mint tűzfal, behatolás megelőző / behatolás detektáló, antivirus és egyéb eszközök finomhangolását valósítjuk meg a SOC-ba érkező adatok elemzésével, adott esetben gépi tanulással támogatott módszerekkel.
A témához kapcsolódó szakdolgozat / diplomamunka témák ITT...
VSOC
A járműelektronika viharos fejlődése az utóbbi évtizedekben egyre több új, elektronikusan támogatott funkció megjelenését eredményezte. A különböző vezérlőegységek immár nem autonóm eszközként működnek, hanem együtt, különböző kommunikációs protokollok segłtségével egy járműelektronikai hálózat kialakítását tették lehetővé. Ez a folyamatos fejlődés megkívánja a kommunikációs technológiák megbízhatóságának, adatátviteli sebességének és az adatok mennyiségének növelését is. Ráadásul az autók internetre csatlakozása újabb követelményeket támaszt az autóiparban használatos protokollokkal, hálózatokkal szemben. Kutatásunk célja a járműelektronikai hálózatok biztonsági analízise.
A témához kapcsolódó szakdolgozat / diplomamunka témák ITT...
Honeypot — Honeypot rendszerek fejlesztése
Egy szervezet hálózati infrastruktúrájának védelmében gyakran használnak ún. Mézesbödön mechanizmust, mely az információs rendszerek illetéktelen használatára vonatkozó kísérletek észlelésére, elhárítására vagy valamilyen módon ellensúlyozására szolgál. E célból gyakran nem csak egy-egy honeypot (Mézesbödön) szervert, hanem több honeypot funkciót, szolgáltatást is magába foglaló rendszereket alkalmaznak. Ezek a rendszerek csapdát állítanak a támadóknak, megpróbálják a figyelmet magukra vonni, valós szolgáltatásokat, környezetet szimulálva. A cél a támadó figyelmének felkeltése és eltérítése a valós hálózat felől.
Kutatásaink fő célja egyrészt a honeypot-ok hatékonyságának mérésére alkalmas keretrendszer elkészítése, illetve a mérőszámok alapján a honeypot-ok optimalizálása.
A SOC-al támogatott hálózatunkba épített honeypot rendszert a hallgatók között hirdetett Capture the flag versenyekkel teszteljük. Itt Honeypot szolgáltatások közé rejtettük a ctf kihívásokat, amelyeket a hallgatóknak adott időintervallumban kell megtalálniuk.
A témához kapcsolódó szakdolgozat / diplomamunka témák ITT...
5G hálózatok biztonsági analízise – 5G SOC fejlesztése
A mobiltávközlés új, 5. generációja rengeteg új lehetőséget kínál nekünk. Azonban a az új technológiai vívmányok természetesen sok új biztonsági fenyegetést is hoznak magukkal. Kutatásunk fő célkitűzése az 5G hálózatok RAN interfészének biztonsági analízise egy erre a célra kialakított 5G laborban. A kutatás során támadó és védelmi oldalról is vizsgáljuk a potenciális sérülékenységeket, illetve egy külön 5G hálózatokra tervezett Bizonsági Műveleti Központ (SOC) felállításával a hálózat monitorozásának lehetővé tétele a cél.
A témához kapcsolódó szakdolgozat / diplomamunka témák ITT...
Támadási gráfok alkalmazhatóságának vizsgálata SOC környezetben
Egy hálózat biztonsági szintjének beazonosításához és javításához elengedhetetlen sérülékenységeinek feltérképezése, biztonsági analízise, kockázati kiértékelése. A kockázatkiérétkelés szempontjából fontos a támadók által kivitelezhető támadási lépések közötti összefüggéseket is átlátni. vizualizálni. A támadási útvonalak reprezentációjára általában fa struktúra alapú vagy gráf alapú modelleket használnak. Azonban ezeknek a módszerekneka a használata skálázhatósági problémát vet fel, illetve a már létező gráf és fa generáló alkalmazások általában nagyon behatárolt eszközkészletűek. Kutatásunk fő iránya saját követelményeinknek megfelelő gráf adatbázisban tárolható támadási gráf generator implementálása, mely a többi kutatási témánk során eltárolt adat beolvasásával, elemzésével, kiértékelésével elősegítia SOC által támogatott funkciók további optimizálhatóságát.
A témához kapcsolódó szakdolgozat / diplomamunka témák ITT...
Cyber Range
A kiberbiztonság területén szerzett gyakorlati tapasztalatok megszerzése és gyarapítása, illetve a kibertámadásokkal szembeni védekezési képességek és biztonsági incidensekre való hatékony és gyors válaszlépések elsajátítása rendkívül nehéz. Habár a kibertámadások száma világszerte soha nem látott iramban növekszik, az egyes munkahelyeken vagy pozíciókban eltöltött idő alatt ezen incidensek száma és változatossága a tapasztalat megszerzéséhez nem elegendő. Ennek kompenzálására a különböző nemzetek, kiberbiztonsági ügynökségek és katonai szervezetek úgynevezett Cyber Range (kiberlőtér) megoldásokat hoznak létre, ahol a résztvevők szimulált környezetben, egyénileg vagy csapatban próbálhatják ki szakmai tudásukat és fejleszthetik képességeiket mind a támadási oldalon (red team), mind pedig a védekező oldalon (blue team).
A témához kapcsolódó szakdolgozat / diplomamunka témák ITT...
Fejlesztés
A Security Operation Center architektúrája:
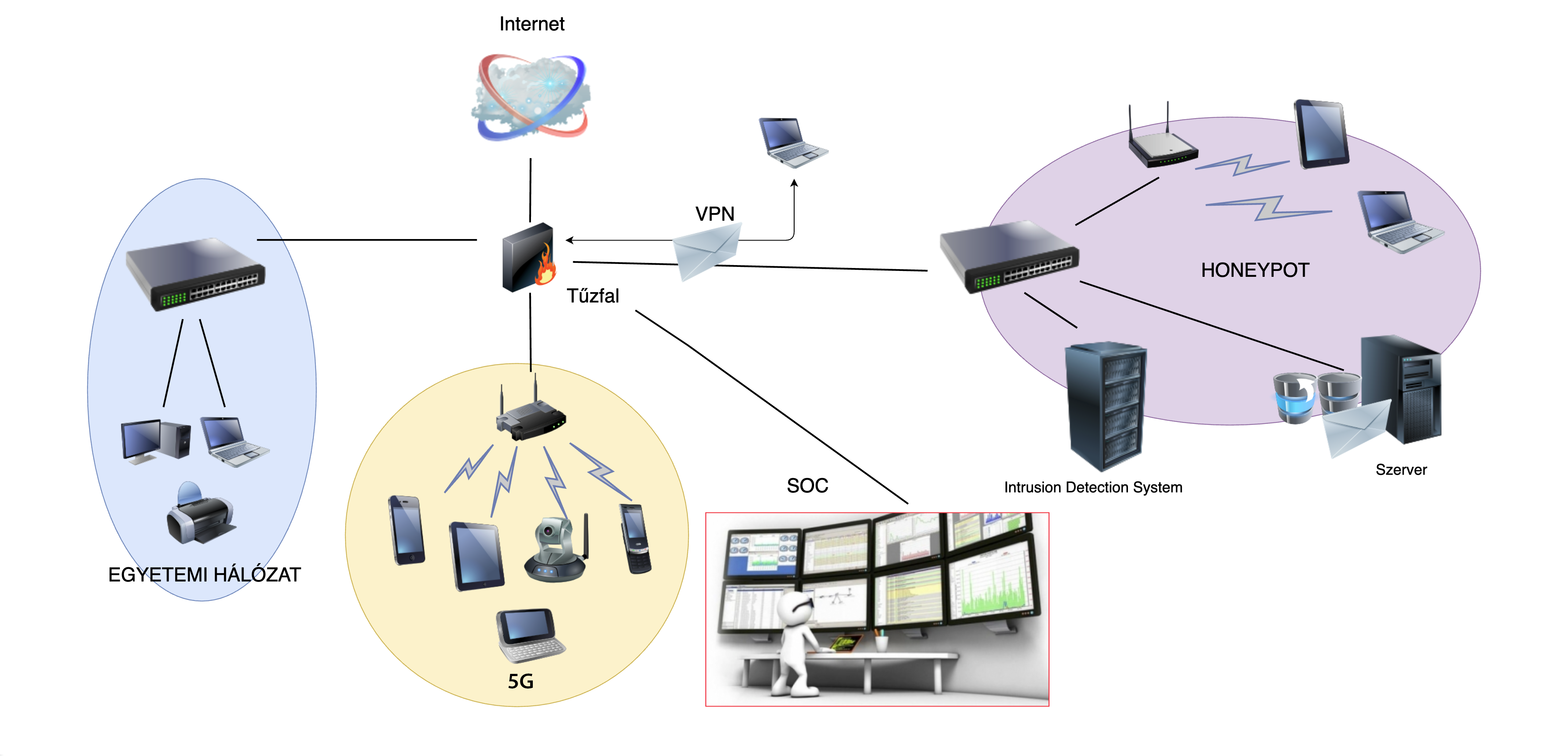
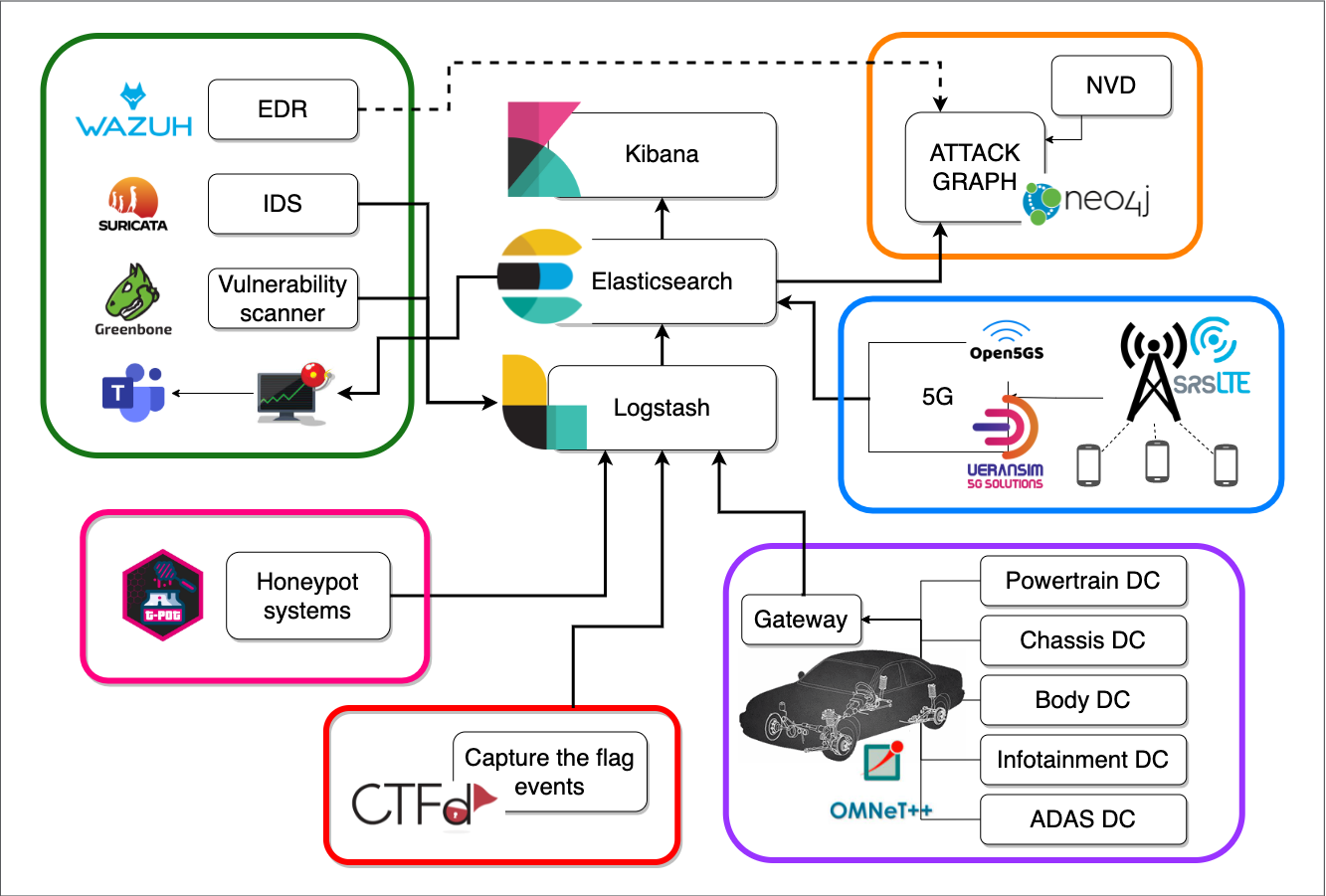
A kialakítandó labor architektúrája:
Publikációk
Szakdolgozatok, diplomamunkák és TDK dolgozatok:
- Orsós Miklós: Biztonsági műveleti központ módszertan kialakítása 5G mobilhálózatokban
- Kecskés Miklós Vilmos: Napló kezelés kialakítása biztonsági műveleti központ használatával 5G hálózatokban
- Kincses László Nándor: Támadások észlelése 5G hálózatokban naplóadatok alapján
- Schmidt Krisztián: Rádiós interfészek sérülékenységei 5G-s hálózatokban
- Berze-Simkó Bálint: Honeypotok alkalmazhatóságának vizsgálata 5G környezetben
- Adámi Bence: SIEM rendszerek adaptálása 5G hálózatokra
- Tóth András: 5G sérülékenységek elemzése biztonsági műveleti központban
- Bánki Máté: Felhasználókezelés tervezése és kialakítása Biztonsági Műveleti Központban, 2023 január
- Szabó Márton Bálint BSc: Webes sérülékenységek elemzése és szimulálása, 2023 január
- Tusor Tamás BSc: Beágyazott rendszerek Kiber-biztonsági vizsgálata az iparban és otthoni környezetben, 2023 január
- Koltai Gábor József BSc: Automotive Ethernet: Biztonsági analízis és tesztelés, 2023 január
- Vereczki András Sándor BSc: Járműelektronikai átjárórendszer: Biztonsági elemzés és értékelés, 2023 január
- Tarr Zsombor BSc: IDS/IPS rendszerek optimalizálása biztonsági műveleti központban, 2023 január
- Leposa Márkó Dániel BSc: Kiberbiztonsági elemző rendszer adatgyűjtő moduljának megtervezése és megvalósítása, 2023 január
- Román Péter BSc: SIEM megoldások, a Biztonsági műveleti központhoz, 2023 január
- Kruppa Ádám BSc: Sérülékenységi vizsgálat biztonsági műveleti központban, 2023 január
- Érsok Máté BSc: Honeypotok szerepe támadások felderítésében, API környezetben, 2022 június
Publikációk
- A. Balogh, M. Érsok, L. Erdődi, A. Szarvák, E. Kail, and A. Bánáti, “Honeypot optimization based on CTF game,” in IEEE 20th Jubilee World Symposium on Applied Machine Intelligence and Informatics SAMI (2022), 2022, pp. 153–157.
- A. Bánáti, E. Rigó, R. Fleiner, and E. Kail, “Use cases of attack graph for SOC optimization purpose,” in 2022 IEEE 26th International Conference on Intelligent Engineering Systems (INES 2022), 2022, pp. 143–147.
- M. Érsok, Á. Balogh, L. Erdődi, M. Kozlovszky, E. Kail, and A. Bánáti, “Measuring Honeypots based on CTF game,” in IEEE 10th Jubilee International Conference on Computational Cybernetics and Cyber-Medical Systems ICCC 2022, 2022, pp. 123–128.
- G. Simon-Nagy, R. Fleiner, and A. Bánáti, “Attack graph implementation in graph database,” in IEEE 20th Jubilee International Symposium on Intelligent Systems and Informatics (SISY 2022), 2022, pp. 127–132.
- M. V. Kecskés, M. Orsós, E. Kail, A. Németh, and A. Bánáti, “5G registration tracking based on logdata,” in IEEE 10th Jubilee International Conference on Computational Cybernetics and Cyber-Medical Systems ICCC 2022, 2022, pp. 129–134.
- N.-E. S. Mera, M. Kozlovszky, Á. Csilling, A. Banati, and B. Abdallah, “Overview of Attack Graph Generation For Automotive Systems,” in IEEE 10th Jubilee International Conference on Computational Cybernetics and Cyber-Medical Systems ICCC 2022, 2022, pp. 135–142.
- M. Orsós, M. V. Kecskés, E. Kail and A. Bánáti, “Log collection and SIEM for 5G SOC,” in IEEE 20th Jubilee World Symposium on Applied Machine Intelligence and Informatics SAMI (2022), 2022, pp. 147–151.
- R. Fleiner, R. Hubert, A. Bánáti, and L. Erdődi, “Security threats based on critical database system privileges,” in IEEE 10th Jubilee International Conference on Computational Cybernetics and Cyber-Medical Systems ICCC 2022, 2022, pp. 117–122.
- H. Ruben, B. Anna, E. László, and F. Rita, “Strengthening Database Security with Capture the Flag Exercises,” in 2022 IEEE 26th International Conference on Intelligent Engineering Systems (INES 2022), 2022, pp. 137–142.
- M. V. Kecskés, M. Orsós, E. Kail, and A. Bánáti, “Monitoring 5G networks in Security Operation Center,” in 21th IEEE International Symposium on Computational Intelligence and Informatics (CINTI 2021), 2021, pp. 223–227.
- D. Mahmoud, A. B. Tóth, E. Kail, and A. Bánáti, “5G Vulnarabilities from Security Operation Center’s Perspective,” in 21th IEEE International Symposium on Computational Intelligence and Informatics (CINTI 2021), 2021, pp. 229–234.
- K. Juhász, V. Póser, M. Kozlovszky, and A. Bánáti, “WiFi vulnerability caused by SSID forgery in the IEEE 802.11 protocol,” in 2019 IEEE 17TH WORLD SYMPOSIUM ON APPLIED MACHINE INTELLIGENCE AND INFORMATICS (SAMI 2019), 2019, pp. 333–338.
- A. Bánáti, E. Kail, K. Karóczkai, and M. Kozlovszky, “Authentication and authorization orchestrator for microservice-based software architectures,” in 2018 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), 2018.
- E. Kail, A. Bánáti, L. Erdődi, and K. Miklós, “Security Survey of Dedicated IoT Networks in the Unlicensed ISM Bands,” in IEEE 12th International Symposium on Applied Computational Intelligence and Informatics (SACI 2018), 2018, pp. 449–454.






